Technology is a part of our daily life and Wireless technology makes our life faster. But, the question is How Can you protect your information when using wireless technology in your every single day.

Wireless technology is a blessing for us. We can communicate with each other and run our business easily with the use of wireless technology. With the advantage of wireless technology, It has some disadvantages too.
From this Content we going to Know about:
- What Is a Wireless Network?
- Types of Wireless Network
- Steps to know How Can you protect your information when using wireless technology?
Here we go...
What is Wireless Network?

Wireless Network is the combination of the network which is not connected with cables. By the use of wireless networks avoid the cost of the internet. How Can you protect your information when using wireless technology? Using a wireless network, you have to maintain your privacy.
The wireless network is based on radio waves, an implementation that takes place at the physical level of network structure.
Types of Wireless Network
Sometimes, we use our personal information on social media and other websites. Hackers use this information for their benefit by harming our personal privacy. In this case, we should follow some privacy rules in wireless technology.

There are four types of wireless networks.
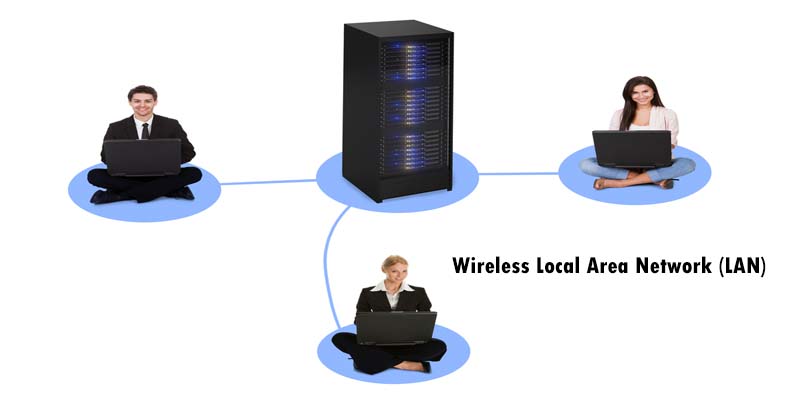
Wireless Local Area Network (LAN):
Connection of links in two or more devices using a wireless distribution method, providing a connection through access points to the wider Internet.
Wireless Metropolitan Area Networks (MAN):

Connects several wireless LANs.
Wireless Wide Area Network (WAN):
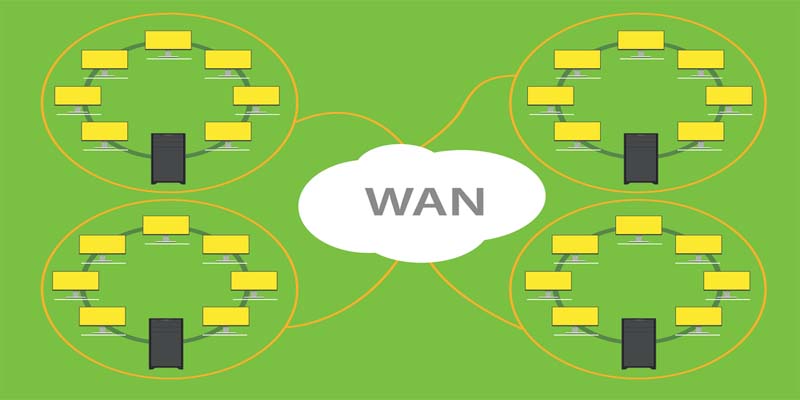
Covers large areas such as neighboring towns and cities.
Wireless Personal Area Network (PAN):

Interconnects devices in a short span, generally within a person’s reach.
Steps to know How Can you protect your information when using wireless technology?

To protect personal information at wireless technology could keep by some privacy maintaining, these are discussed step by step:
1. Keep Passwords Private
Using strong passwords in the laptop, credit, bank, and other accounts. In the Arrangement of Password be use different characters.. For example, “I catch two Birds from the tree” could become 1C2Bt.
2. Securing Your Social Security Number
Social security numbers must be included for privacy. Some related questions should adjust to topics if someone asks you to share our SSN. The social security number system should be included with a strong password and number.
3. Safely Dispose of Personal Information
Get rid of all the personal information it stores Before you dispose of a computer. To overwrite the entire hard drive use a wipe utility program. Check your owner’s manual and the service provider’s website before you dispose of a Mobile phone device. Hide the memory or the subscriber identity module (SIM) card from a mobile device. Remove all the list of calls made and received.
4. Be Wise About Wi-Fi
Before connecting with the Wi-Fi network, keep your personal privacy. Know about the Wi-Fi connection, If it is free for all Personal information over your laptop or smartphone on a public wireless network in a coffee shop, library, airport, hotel, or another public place, see if your information will be protected to this site before sending it. If we use an encrypted website, it protects only the information we send to and from that site.
5. Lock Up Your Laptop
Business and financial information should be kept on your laptop only when necessary. You Shouldn’t Use an automatic login feature that saves your user name and password and always logs off when you’re finished. In that case, if your laptop is stolen, it will be harder for a thief to get at your personal information.
6. Using a VPN
Virtual Private Network is used in many companies and organizations. When away from the office VPN allows employees to connect securely to their network. VPNs encrypt connections at the receiving and sending and keep out traffic.
7. Be Aware of Your Surroundings
You should be aware of what’s going on around you When using a public wireless access point. Can others view your screen? If someone saw your information it may be caused by hacking your information.
8. Unauthorized Computer Access
Wireless network combined with an unsecured file which can be the reason for hacking your information.. Computer program which is dangerous for personal information security. It should be removed from the computer system. Avoid unauthorized computer access into the computer system.
9. Make Your Wireless Network Invisible
A free wireless network is risky for sharing personal information. Wireless networks should state with hiding passwords. Make your network system invisible and personal area based.
10. Use File Sharing with Caution
File Sharing in an unknown place is dangerous for personal information. Confirmed about these sites before sharing any file on those sites. Well known Website and defendable social network is the first condition for sharing your information.
11. Use Security Software
Before using a wireless network, you should install antivirus software, anti-spyware software, and a firewall. Set all the related information to update these protections often. Protect your information with the security software installed.
12. Avoid Publishing Email
Avoid opening files, clicking on links, or downloading programs sent by strangers. Opening an unknown file from someone you don’t know could harm your system to a computer virus or spyware that captures your passwords or other information you type.
Conclusion
Wireless technology made our communication system very easy and updated. ‘How Can you protect your information when using wireless technology is the key to knowing the answer for that you can take a position and possible best step to protect the information on wireless technology. Wireless technology is also risky for hampering our personal information. People who use this technology should be aware of their privacy in online systems.
References: